Cybersecurity researchers from ESET on Thursday said they took down a portion of a malware botnet comprising at least 35,000 compromised Windows systems that attackers were secretly using to mine Monero cryptocurrency.
The botnet, named "VictoryGate," has been active since May 2019, with infections mainly reported in Latin America, particularly Peru accounting for 90% of the compromised devices.
"The main activity of the botnet is mining Monero cryptocurrency," ESET said. "The victims include organizations in both public and private sectors, including financial institutions."
ESET said it worked with dynamic DNS provider No-IP to take down the malicious command-and-control (C2) servers and that it set up fake domains (aka sinkholes) to monitor the botnet's activity.
The sinkhole data shows that between 2,000 and 3,500 infected computers connected to the C2 servers on a daily basis during February and March this year.
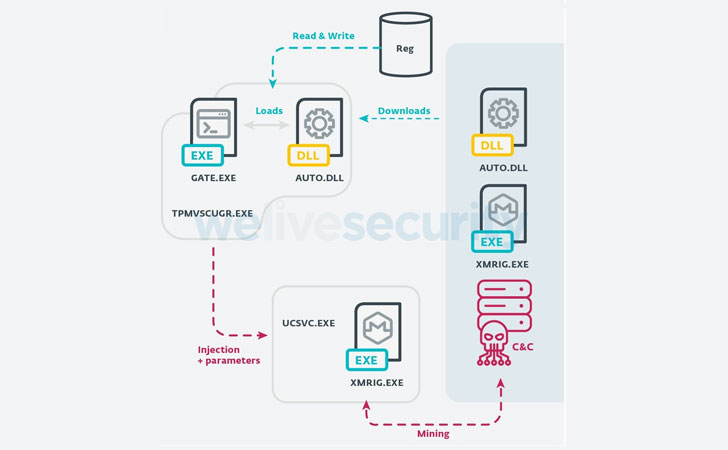
According to ESET researchers, VictoryGate propagates via removable devices such as USB drives, which, when connected to the victim machine, installs a malicious payload into the system.
In addition, the module also communicates with the C2 server to receive a secondary payload that injects arbitrary code into legitimate Windows processes, such as introducing XMRig mining software into the ucsvc.exe process (or Boot File Servicing Utility), thus facilitating Monero mining.
"From the data collected during our sinkholing activities, we can determine that there are, on average, 2,000 devices mining throughout the day," the researchers said. "If we estimate an average hash rate of 150H/s, we could say that the authors of this campaign have collected at least 80 Monero (approximately $6000) from this botnet alone."
With USB drives being used as a propagation vector, ESET warned of new infections that could occur in the future. But with a significant chunk of C2 infrastructure sinkholed, the bots will no longer receive secondary payloads. However, those that were compromised before the C2 servers were taken down would still continue to mine Monero.
"One of the interesting characteristics about VictoryGate is that it shows a greater effort to avoid detection than previous, similar campaigns in the region," the research team concluded.
"And, given the fact that the botmaster can update functionality of the payloads that are downloaded and executed on the infected devices from crypto mining to any other malicious activities at any given time, this poses a considerable risk."


0 Comments